Quiz: module 02 threat management and cybersecurity resources – Welcome to our comprehensive guide to threat management and cybersecurity resources. In today’s digital landscape, understanding and mitigating cybersecurity threats is paramount for individuals and organizations alike. This quiz will provide you with the knowledge and tools necessary to protect your data, systems, and networks.
Threat Management and Cybersecurity Resources Overview
In today’s digital landscape, where sensitive data and critical systems are increasingly targeted by cybercriminals, threat management and cybersecurity have become paramount. This article provides a comprehensive overview of threat management and cybersecurity resources, empowering individuals and organizations to protect their digital assets and maintain their resilience against cyberattacks.
Threat management involves identifying, assessing, and mitigating potential threats to an organization’s information systems, networks, and data. Cybersecurity, on the other hand, focuses on protecting these assets from unauthorized access, use, disclosure, disruption, modification, or destruction.
Available Resources for Threat Management and Cybersecurity
- National Institute of Standards and Technology (NIST) Cybersecurity Framework: Provides guidance on best practices for cybersecurity risk management.
- Center for Internet Security (CIS) Controls: Offers a set of security controls to protect against common cyber threats.
- International Organization for Standardization (ISO) 27001: An international standard that Artikels requirements for an information security management system (ISMS).
- Cybersecurity and Infrastructure Security Agency (CISA): Provides resources and guidance on cybersecurity threats and best practices.
- Information Security Forum (ISF): A global organization that shares knowledge and best practices on information security.
Understanding Cybersecurity Threats
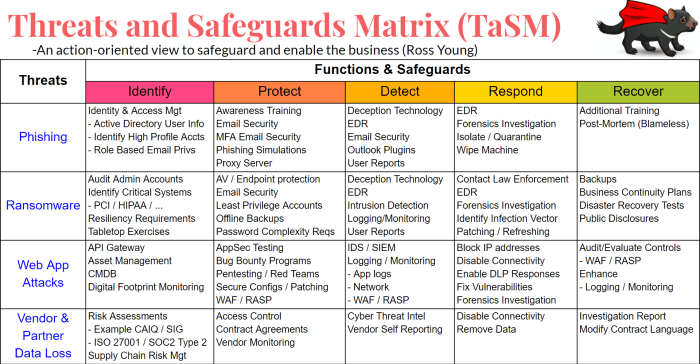
Cybersecurity threats are constantly evolving, posing significant risks to individuals and organizations. It is crucial to stay informed about these threats and understand their potential impact.
Common Cybersecurity Threats
- Malware: Malicious software that can damage or steal data, disrupt systems, or spy on users.
- Phishing: Attempts to trick users into revealing sensitive information, such as passwords or credit card numbers.
- Ransomware: Encrypts data and demands payment in exchange for decryption.
- Social engineering: Exploits human weaknesses to manipulate users into performing actions that compromise security.
- Zero-day attacks: Exploits vulnerabilities that are unknown to software developers and security researchers.
Importance of Staying Informed
Staying informed about emerging cybersecurity threats is essential for effective protection. This includes monitoring news and industry reports, attending cybersecurity conferences and webinars, and subscribing to security alerts from trusted sources.
Implementing Cybersecurity Measures
Implementing robust cybersecurity measures is crucial for protecting organizations from cyberattacks. A comprehensive approach involves securing networks, devices, and data, as well as educating employees about cybersecurity best practices.
Step-by-Step Guide
- Secure Networks: Implement firewalls, intrusion detection and prevention systems (IDS/IPS), and virtual private networks (VPNs).
- Secure Devices: Install antivirus and anti-malware software, keep operating systems and software up to date, and use strong passwords.
- Secure Data: Encrypt sensitive data, implement data backup and recovery plans, and restrict access to data on a need-to-know basis.
- Educate Employees: Train employees on cybersecurity threats and best practices, including password management, phishing awareness, and social engineering.
Best Practices for Securing Passwords, Quiz: module 02 threat management and cybersecurity resources
- Create complex passwords with a minimum length of 12 characters.
- Use a combination of upper and lowercase letters, numbers, and symbols.
- Avoid using personal information, such as names or birthdates.
- Change passwords regularly and do not reuse old ones.
- Use a password manager to securely store and manage passwords.
Threat Monitoring and Response
Monitoring for potential threats and vulnerabilities is essential for timely detection and response. This involves using security tools and technologies, as well as establishing clear incident response plans.
Importance of Monitoring
Continuous monitoring allows organizations to identify suspicious activity, detect potential breaches, and respond promptly to mitigate the impact of cyberattacks.
Security Tools and Technologies
- Security Information and Event Management (SIEM) systems: Collect and analyze security data from various sources.
- Intrusion Detection Systems (IDS): Detect unauthorized access or activity on networks and systems.
- Vulnerability Scanners: Identify weaknesses in systems and software that could be exploited by attackers.
Incident Response Plans
Incident response plans Artikel the steps to be taken in the event of a cybersecurity breach. They should include:
- Roles and responsibilities of key personnel.
- Procedures for containment, eradication, and recovery.
- Communication protocols with internal and external stakeholders.
Employee Cybersecurity Awareness
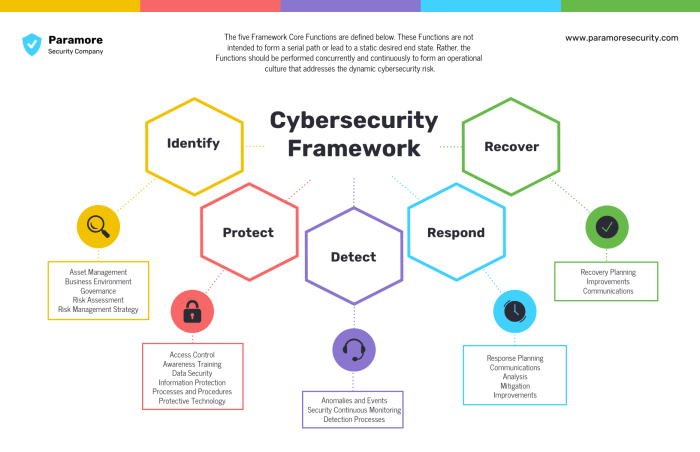
Employees play a vital role in maintaining cybersecurity. Educating them about threats and best practices is essential for reducing the risk of successful attacks.
Educating Employees
- Conduct regular cybersecurity training sessions.
- Provide resources and materials on cybersecurity threats and best practices.
- Encourage employees to report suspicious activity and potential security breaches.
Importance of Reporting
Empowering employees to report suspicious activity allows organizations to identify and address potential threats early on, minimizing the risk of a successful cyberattack.
Legal and Regulatory Considerations: Quiz: Module 02 Threat Management And Cybersecurity Resources

Organizations must comply with relevant legal and regulatory requirements related to cybersecurity. Failure to do so can result in penalties and reputational damage.
Legal and Regulatory Requirements
- General Data Protection Regulation (GDPR): Protects personal data of individuals within the European Union.
- Health Insurance Portability and Accountability Act (HIPAA): Protects the privacy and security of health information in the United States.
- Payment Card Industry Data Security Standard (PCI DSS): Protects sensitive data related to payment cards.
Consequences of Non-Compliance
- Financial penalties.
- Legal liability.
- Reputational damage.
Importance of Legal Advice
Organizations should seek legal advice to ensure compliance with relevant laws and regulations. This can help mitigate risks and protect against potential legal consequences.
FAQ Overview
What are some common types of cyberattacks?
Malware, phishing, ransomware, DDoS attacks, SQL injection
How can I create a strong password?
Use a combination of upper and lowercase letters, numbers, and symbols. Avoid using personal information or common words.
What should I do if I suspect a cybersecurity incident?
Report the incident to your IT department or security team immediately. Do not open suspicious emails or click on unknown links.